V2X priority
V2X priority is a use case allowing a vehicle or user to request priority near an intersection.
Several hardware elements will be installed in order to make this system work :
- A Road Side Unit (RSU) installed near the intersection
- An On Board Unit (OBU) installed on board vehicles
- The ITS platform, a server installed in the RSU network or in the Cloud
- A traffic light controller to manage the traffic light plan and the switching on of traffic lights
- The APP platform, a server installed in the Cloud
- A smartphone with the priority app (can be used in the car, on foot or on a bicycle)
Vehicles and users
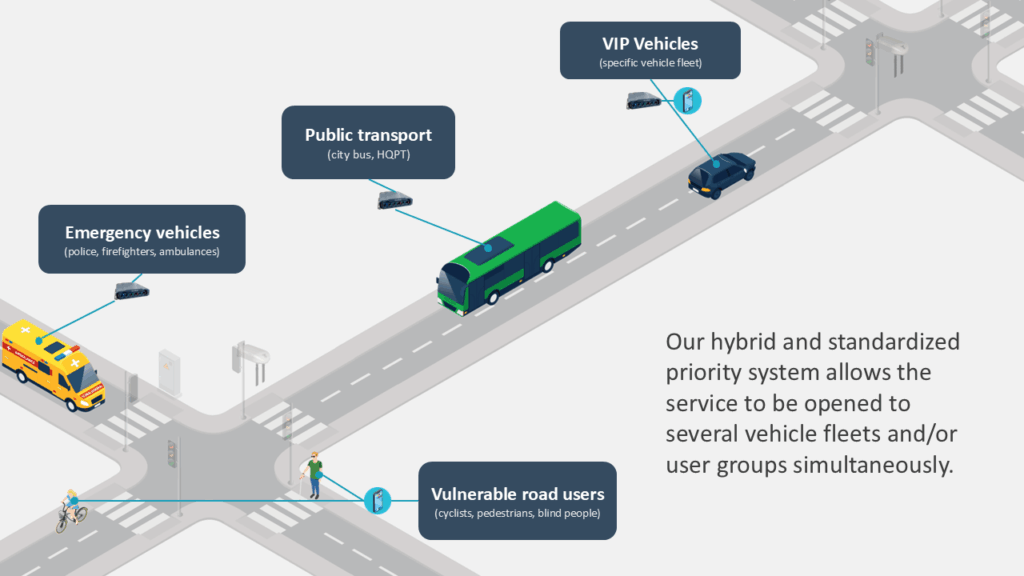
Vehicle trigger modes

Connection via an Operating Assistance System (by approach curve)
The On Board Unit triggers a priority request at one or more intersections in a row along the route. The approach time depends on the statistical approach curve and takes into account the advance/delay of the schedule as well as known stops. This operation is suitable for buses.
The onboard NeoGLS software includes an API to be implemented by the SAE.
In the case of simultaneous requests, only the traffic controller has the final decision. Depending on the implementation of the traffic controller dialogue, it is possible to define an importance level for each vehicle.
The RSU can also filter requests by vehicle type.
The V2X range is at least 500m in urban areas, which guarantees sufficient approach time for the traffic light controller.
In the case of a priority request at several intersections upstream, the ITS platform takes over if the following RSUs are out of V2X range (e.g., after a turn, behind a tall building).
Supported traffic light controllers

Standards and security
V2X communication is based on European standards validated by ETSI :
- ETSI EN 302 636-4 (GeoNetworking)
- ETSI EN 302 637-2 (CAM)
- ETSI TS 103 301 (SREM, SSEM, MAPEM)
With the MQTT protocol, hybrid transmissions use these same messages.
The security of V2X transmissions is based on digital signatures, according to the ETSI TS 103 097 standard. It guarantees the authenticity of the sender and the integrity of the messages.
All IP communications use TLS encryption (HTTPs, MQTTs).
Log uploading is secured by SCP, and maintenance operations are performed via SSH. Monitoring uses SNMPv3.
